Importance Of CyberSecurity
As time has moved on, technology has come on leaps and bounds, leading to more of our digital assets and sensitive information being saved online. Due to threats in the current online world, the importance of cyber security cannot be overstated. This blog will explore the role that cyber security plays in today’s society and why it’s so important.
Cyber security is the process of protecting our networks, devices and computer systems from cyber attacks. Cyber attacks are becoming smarter and with new methods powered by social engineering and artificial intelligence they are an increasingly evolving danger to your personal information. As we are introducing more technology, intelligent cloud security solutions should be implemented alongside strong password policies like multi-factor authentication to avoid unauthorised access.

In today’s world, our personal information has become a precious commodity. Financial data, conversations and details leave a digital footprint which is open to exploitation and that is what cyber security exists to protect. Cyber security measures act as a shield, ensuring that our private information remains private; through encryptions and secure apps/websites, cyber security helps to build a virtual fortress around our personal lives.
“Phishing” refers to an attempt to steal sensitive information, typically in the form of usernames, passwords, credit card numbers, bank account information or other important data to utilise or sell the stolen information. They act as a reputable source, by sending out emails in the hopes that even one person will click the link and provide their information.
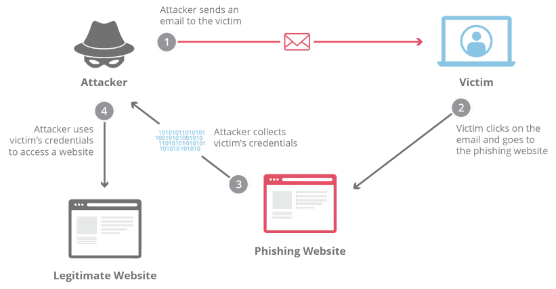
There are ways to spot when an email is a scam for example simple spelling mistakes or changes to domain names when clicking the link in the email. In addition to this, all users should stop to think about why they would be receiving an email like this. The most effective way to prevent phishing attacks is to use two-factor authentication as it adds an extra layer of sensitive information when logging into sensitive applications.
A malware attack is a common cyberattack where malware (usually malicious software) executes actions on the victim’s system. It can involve stealing data, credentials, payment information and more and is extremely costly to anyone who falls victim.
There are three main types of malware attacks :
- Trojan Horse – This is a program which appears to be one thing but is in fact a delivery mechanism for malware. It relies on the user to download via the internet or an email attachment and attacks the target.
- Virus – A virus is a form of malware which infects other programs/files of a target through code injection. Unlike a trojan horse, a virus can replicate itself and enter into multiple different programs and files.
- Worms – A worm is a malware designed to propagate itself into other systems. While virus and trojan horse malware are localised to one infected target system, a worm is put in place with the intention of infecting other targets.

The best way to defend yourself against these types of attacks is by training users on the best practices for avoiding malware as well as knowing how to identify potential malware. It may sound simple however it is the most effective method of protecting yourself. In addition to this, ensuring your network is secure as well as using reputable A/V software (which can detect and remove any existing malware on a system) will massively reduce the risk of being affected.
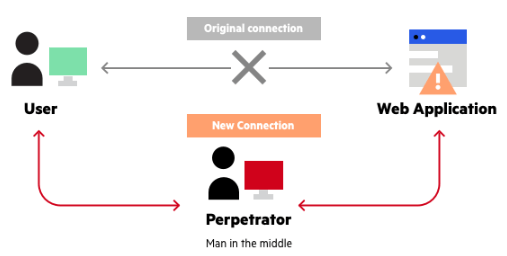
A man-in-the-middle attack is when a perpetrator positions themselves in a conversation between a user and an application – either to eavesdrop or to impersonate one of the parties. The intention is to steal personal information such as login credentials, account details and credit card numbers. The obtained information could be used for a multitude of things including identity theft, bank transfers or password changes.
The best ways to prevent these catastrophes from occurring are :
- Avoiding Wi-Fi connections that aren’t password-protected
- Paying attention to browser notifications reporting a website as being unsecured
- Immediately logging out of a secure application when its not in use
- Not using public networks when conducting sensitive transactions
As the prevalence and sophistication of cybersecurity attacks continue to grow, we need to do everyone we can to best protect ourselves. Understanding the various threats and how they come to be is the first step in preventing them from harming you and staying informed on how we can collectively build a stronger defence has become more important. However, as cyberattacks evolve, our security measures will too so the key thing to remember is to stay vigilant!